Zero Trust challenges the “castle and moat” model of traditional networks. This new approach assumes all users and devices are potential attackers and requires constant monitoring, re-verification, and multi-factor authentication. It also requires network segmentation and application control to limit the attack surface.
Zero Trust Defined
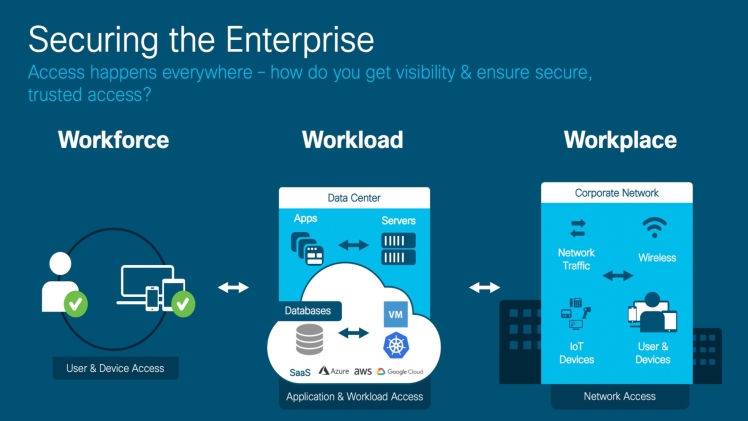
Zero trust network access control is an approach to network security that works from the ground up. It’s built on “never trust, always verify.” Every device, user, and application is untrusted until proven trustworthy. It’s a security model that addresses many modern challenges businesses face, like remote workers, hybrid cloud environments, and ransomware threats. Zero Trust is built on several technologies, including identity management, access control, and networking. It uses a “microperimeter” to separate critical assets from untrusted resources. This helps to reduce the attack surface and protects against threats by ensuring that only valid users can access sensitive data. It also uses continuous authentication and access control to ensure that users only connect to what they need to do their job. It also uses micro-segmentation to ensure each data set has different access rules. This helps prevent hackers from stealing information across networks and makes tracking activity more accessible. Zero Trust has become a popular solution for organizations looking to improve their security infrastructure. According to a recent survey, 55% of respondents said that an increase in ransomware attacks drove their Zero Trust strategy, and 32% were motivated by concerns about remote workers and supply chain threats.
Importance
With remote work and mobile devices making accessing company data and applications more accessible from anywhere, security teams must protect these assets as they ebb and flow across the network. Zero Trust helps secure these dissolving perimeters by requiring granular authentication, authorization, and real-time device, user, and application activity monitoring. It also uses new security technologies like multi-factor authentication (MFA) to verify identities and restrict access to resources to only those who can prove they are who they say they are. For example, employees logging into a website or a mobile app with their password must also enter a code sent to a separate device, such as their phone, to gain access. This enables a much higher level of protection and minimizes risk by ensuring only those authorized to access sensitive information can do so. The Zero Trust model also limits the “blast radius” of any breach should one occur, allowing systems and people to respond and limit damage quickly. For example, if someone in the accounting department used stolen credentials to access a credit card number database, the system could immediately identify them and stop their entry before they could do any damage. This approach requires more advanced capabilities than what many organizations have today. Still, increasing security in an age of shrinking and expanding networks, mobile devices, and cloud services is necessary.
Benefits
Zero Trust takes a software-defined approach to security and eliminates network-based assumptions about a resource’s identity or location. It protects data, workflows, and applications using business policies regardless of the location of the resource or where it communicates—in public clouds, hybrid environments, containerized workloads, and even on-premises infrastructure. This enables organizations to enable digital transformation while protecting business information and assets safely. Zero Trust also includes visibility and control over users, devices, and traffic to help enforce the principle of least privilege, ensuring that access is granted only to those with a legitimate need. The architecture monitors user and device identity, credentials, and security posture to prevent unauthorized access. It also uses the principle of continuous validation to continuously verify and authenticate users and their devices and apply the principle of least privilege to applications and services based on the need to do so.
Additionally, Zero Trust allows organizations to deploy single sign-on tools for end users that reduce the number of passwords they must keep track of. This simplifies how they access the resources they need and helps reduce the risk of password mismanagement attacks. The benefit of a zero-trust approach is that it eliminates the need to secure a defensible perimeter. Instead, the protection travels with the workload to wherever it goes, so the defenses are more robust wherever the threats are. This is a crucial advantage over traditional network-based security, which typically relies on static segmentation to secure the data center.
Challenges
Implementing Zero Trust can be challenging for many organizations. It requires a thorough understanding of the network’s intricacies, including all users, devices, and applications. Additionally, organizations must identify all security software and policies. In addition, a zero-trust model may require substantial changes to the infrastructure. This can create a time lag before full benefits are realized. Zero Trust also requires a strict definition of permissions. This can be difficult since the staff constantly changes: people are hired, promoted, transferred, reassigned, or laid off. As a result, permissions must be updated regularly to maintain accurate and adequate security. In the event of a security breach, zero Trust can make it easier to identify the source by limiting visibility to only the application or server involved in the attack. This minimizes the impact of a malicious insider, which is often harder to detect than a malicious outsider. Zero Trust relies on continuous verification and a reduction in the “blast radius,” which is the area that needs to be protected. This can be a challenge for some organizations, mainly if their employees are used to working with the old method of accessing applications and data. Regular training and clear communication can help alleviate employee concerns and resistance. Then, a smooth transition can be achieved without interrupting business as usual.